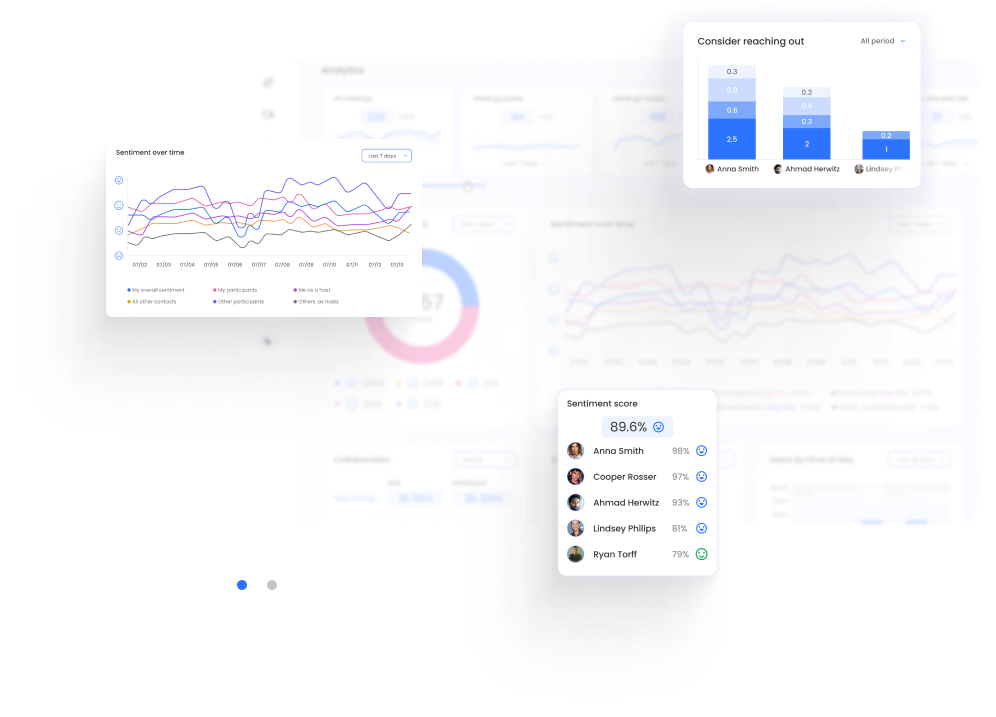
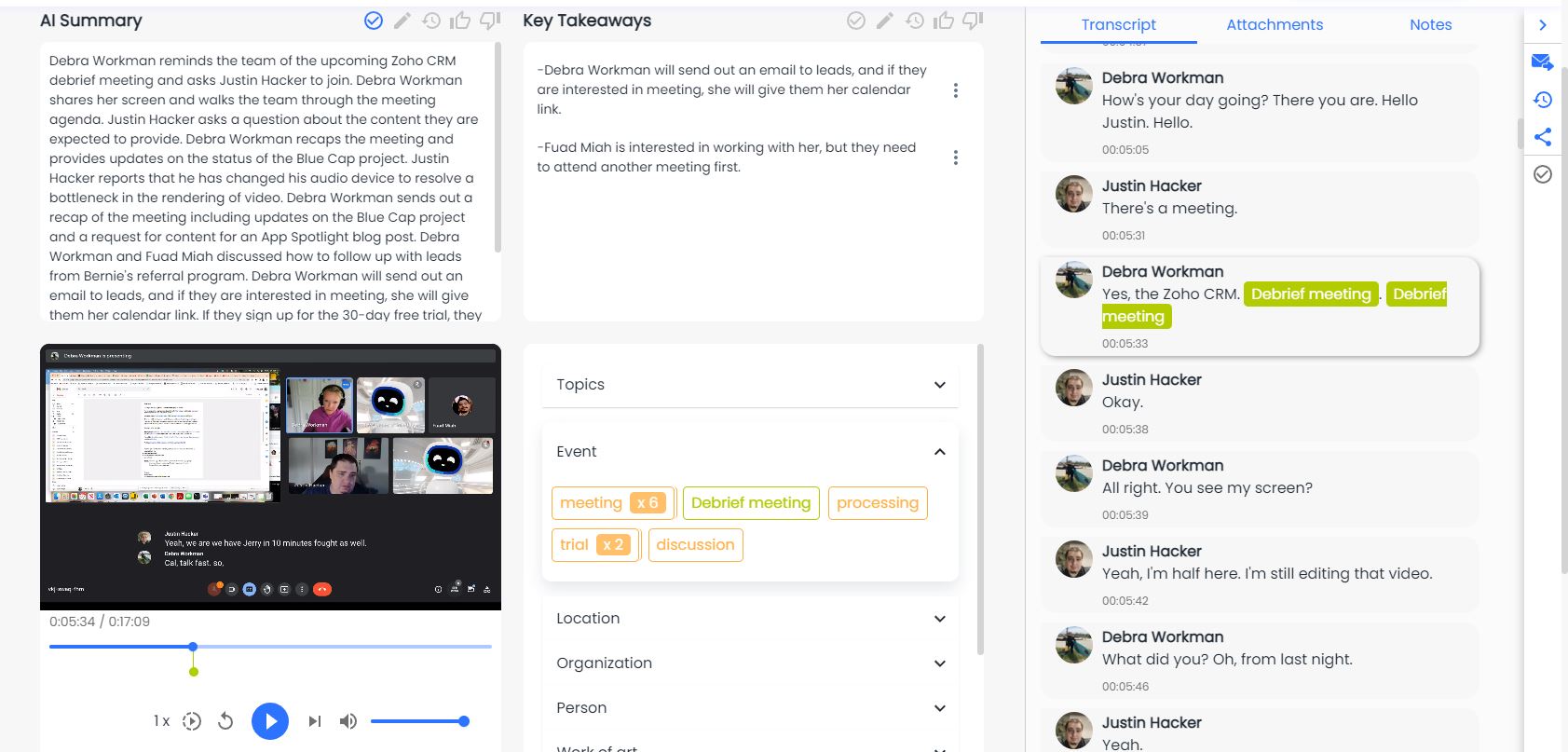
Automate Relationship Intelligence At Scale
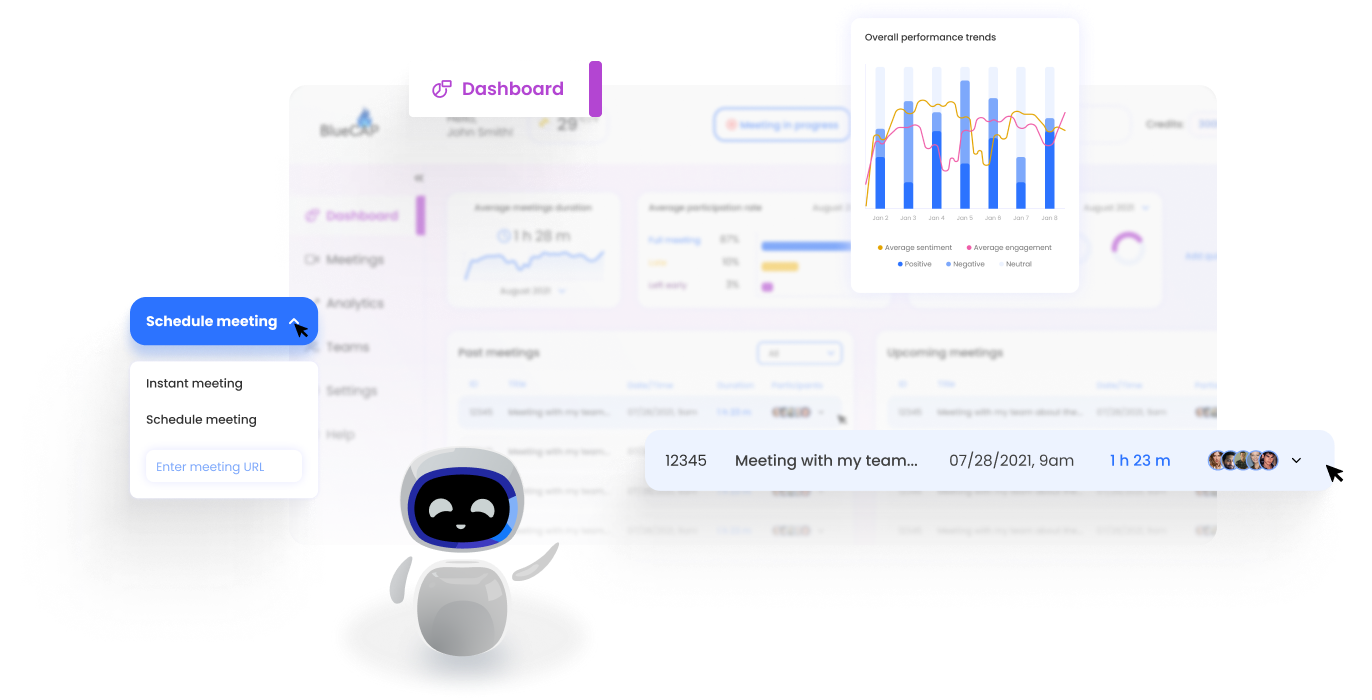
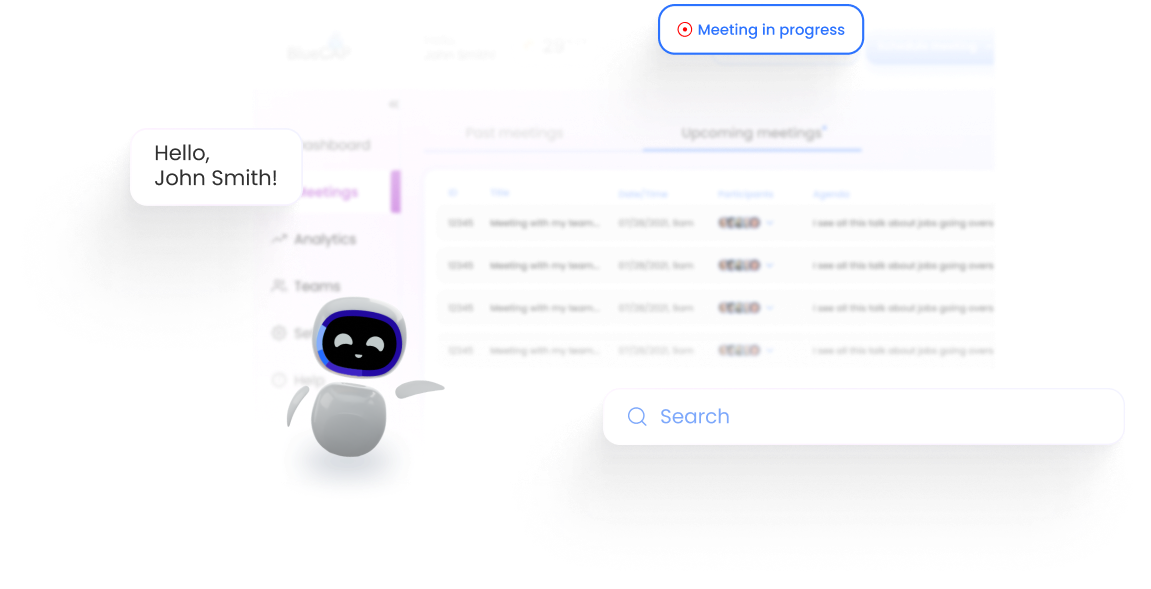
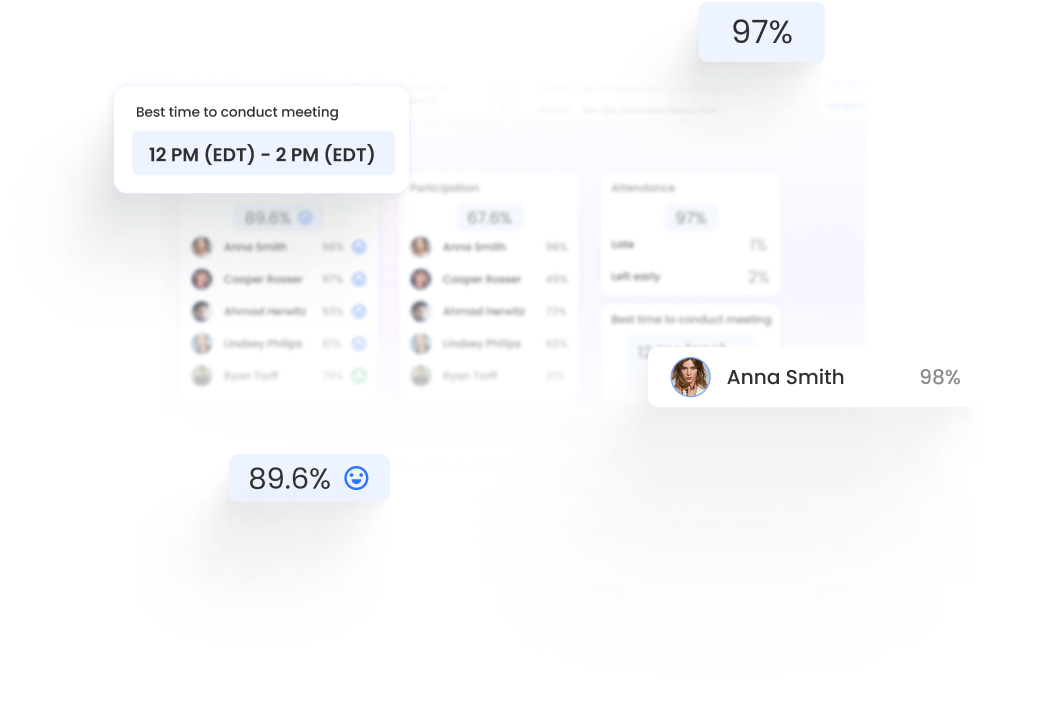
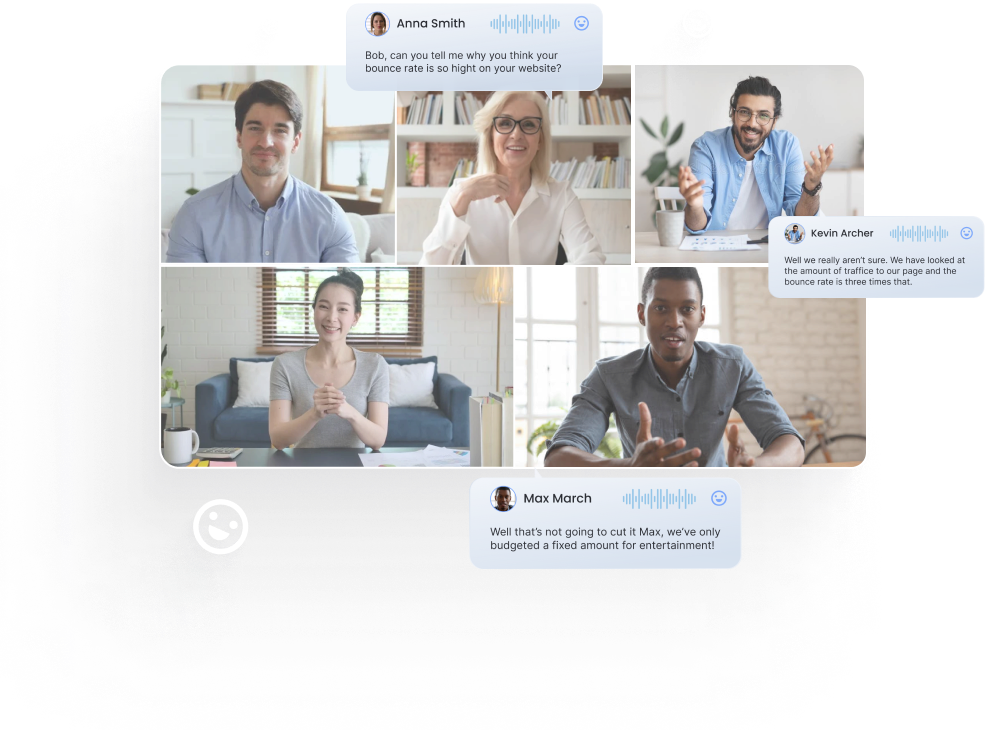
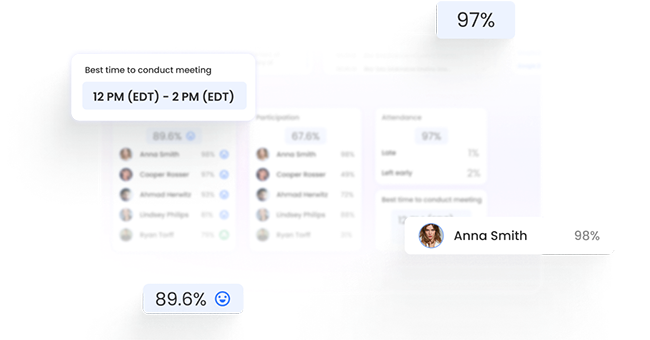
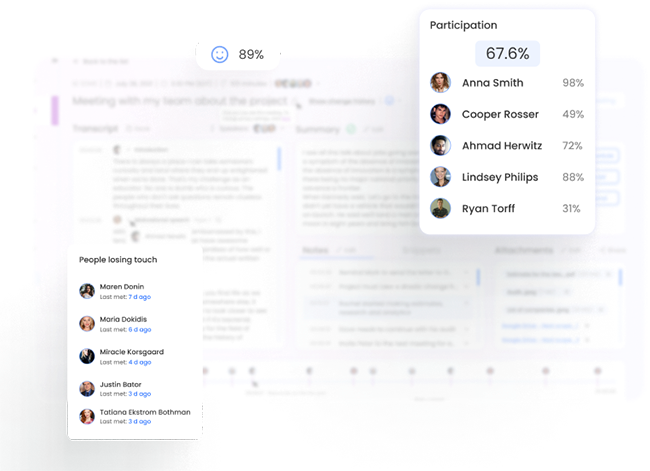
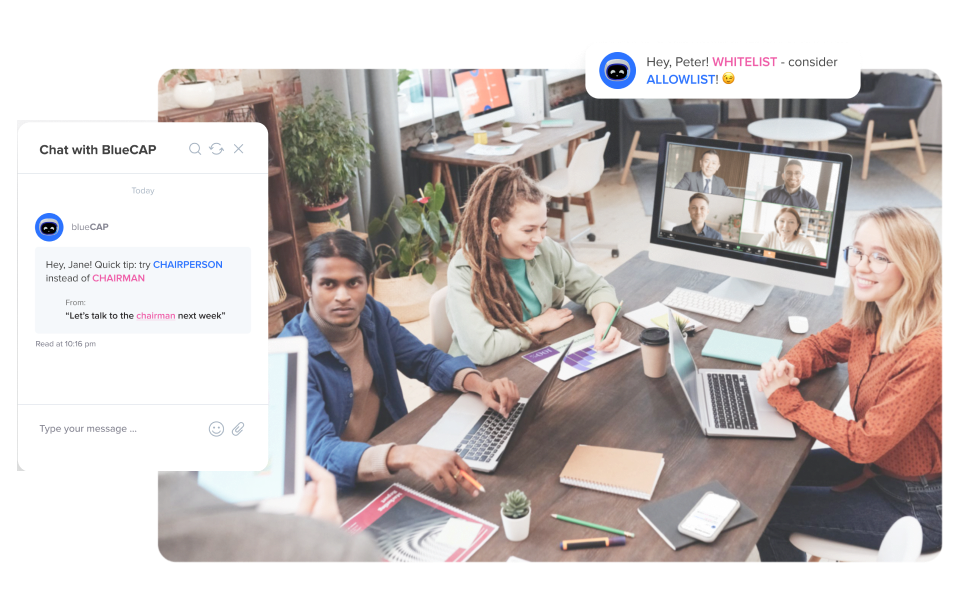
Through a deep A.I. understanding of language, emotion, and human behaviour, bluecap™ empowers enterprises to augment capabilities. Measure and nurture relationships with empathy, enhance corporate culture and harmonize better outcomes.
Book A Demo